TRON is famous for its astonishing TPS and extremely low fees, turning it into a global center for activities such as USDT moving. Interaction with TRON is usually an easy-peasy, top-down experience for a majority of users: hit send, confirm the transaction, and watch it confirm within seconds — yet behind this facade is a complex but powerful technical architecture, a ballet of cryptography, consensus, and resource management entities. What happens behind the scenes, really, when you send a transaction? However, what is this TRON address made from — its cryptographic backbone? And how exactly does the network decide on where its limited Energy and Bandwidth needs to be spent?
In this guide, you will take a broader deep dive into the engine room of TRON network. We'll go beyond the superficial we will be dismantling the reassuring veil of technical mumbo-jumbo that makes your transactions fast AND magically secure. This understanding (and more) forms the base level of knowledge that developers should be striving for — but is also an empowering base level for any user who wants to use the ecosystem in a safer, more efficient, and more confidently manner when using advanced services that take advantage of these fundamental mechanics in new and complex ways.
Breakdown of a TRON Transaction: From Creation to Confirmation
Sending tokens on TRON initiates a process that can be split into three distinguishable, consecutive stages. This procedure is the basis of nearly all blockchains, and the intricacies of this system are essential to understand when grasping the underlying state of security which strengthens the network.
Forming
Your wallet software, which represents your agent, prepares the raw data for the transaction. It's not just who sent it, who it was sent to, and for how much. This includes a number of other fields which are of utmost importance to maintaining security and order:
- ref_block_bytes and ref_block_hash: These fields provide an anchor, binding the transaction to a recent, specific block on the blockchain. This stops an attack vector where a tx could be replayed on other forks of the chain.
- expiration: This is a timestamp that indicates a period of time the transaction is valid for. The network will drop the transaction if it is not included in the block before this duration. This is also, similarly, another key security measure to keep bad actors from rebroadcasting old, confirmed transactions at a later date.
- fee_limit: It is the highest number of TRX the user is ready to consume to have some Energy (only if his proposed resource amount is not enough).
Signing
This is the essence of security of the blockchain. Your unique private key cryptographically "signs" the fully formed transaction data. TRON, is also based on ECDSA and is used in Bitcoin and Ethereum (secp256k1). The output of this algorithm is a unique string of characters known as a digital signature and it provides an unbreakable mathematical proof that the owner of the private key signed this exact transaction. Just a change of a single byte in the transaction data would lead to a completely new signature.
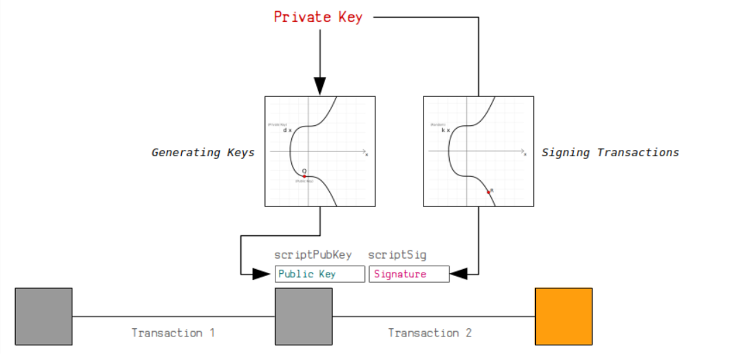
This is the reason why hardware wallets such as ledger are offering such a high level of security. The transaction is constructed on your possibly insecure computer, yet then delivered to the hardware wallet where it is signed in a secure, isolated chip. Such private keys never go off the devices, which means it becomes safe from all other online injuries.
Broadcasting and Propagation
After the transaction is signed, it is now a secure and unalterable envelope. Your wallet then sends it out to the TRON network. It does not mean that it is sent to a central server. It then gets relayed into a handful of "peer" nodes your wallet connects to. Next these nodes will then verify the signature and send the transaction to the peers they are connected to. And so it continues, spreading through the peer-to-peer network like a ripple in a pond until it reaches the network's official validators — the Super Representatives.
Exploratory First Principles: What are Addresses, Confirmations and Finality
Having an understanding of the transaction lifecycle, we will now be able to break down into more specificity two of the common technical terms.
An address on the TRON network is your public identity. That repetitive alphanumeric sequence which starts with the letter T is not a coincidence; it is the result of Base58Check encoding of a public key hash. This encoding scheme is straightforward and it's relatively easy to operate without making a mistake as a human. It uses an alphabet that excludes visually ambiguous characters (e.g. '0' and 'O', or 'I' and 'l'), and employs a checksum by default. Since a check sum will fail if you make a small typo when entering a TRON address, a properly designed wallet will catch this mistake right away and will not allow you to send funds to a non-existent address.
Confirmations and Finality
When someone talks about your transaction having a certain number of confirmations, they are referring to how many blocks have been added to the chain after the block containing your transaction. Thanks to its DPoS consensus mechanism, TRON can achieve near-instant finality. One new block gets generated every 3 seconds. In order for a transaction to be 99.9% irreversible, it must be confirmed by at least two-thirds of the 27 Super Representatives.
It usually happens after around 19-20 blocks, which takes approximately a minute. They call this "finalized" state, which is around a million times harder to later change or roll back than what you can get from Proof-of-Work chains such as Bitcoin, where finality is only probabilistic and its much harder gains as well.
Super Representatives and Generating Resources – the Engine Room
These computers are known as 27 Super Representatives (SRs) and are responsible for validating transactions and managing network resources. However, these are more than servers — they are the elected governors of the TRON network, helping to keep the blockchain healthy and scalable.
Energy and Bandwidth generate this system directly. Here's a more detailed breakdown:
Bandwidth: the whole TRON network creates a certain amount of Bandwidth points every 24 hours. Part of this is distributed at no cost to all live accounts. The remaining portion is spread evenly among all users who have frozen their TRX in exchange for Bandwidth. In a nutshell, Bandwidth is a resource for the size of transaction data. You are paying for the storage of your transaction within a block.
Energy: this resource is an unfixed pool unlike the Bandwidth. This is a measure of how much computational work the TRON Virtual Machine (TVM) needs to perform to execute a smart contract. For example, a basic TRX movement does not require interaction with a smart contract, hence it costs 0 Energy. More intricate DeFi actions that requires iterations of different contract calls will burn many Energy. The TRX you freeze for Energy give your account an "Energy limit" which means you share your portion with the TRX for Network is available for computing power.
It is this dual-resource model that makes TRON so efficient. Divides the cost of data storage (Bandwidth) and this of computation (Energy) This paved the path to a secondary market, the Tron Energy rental services business, where wealthier users who have large amounts of Energy can rent the additional Energy they don't use out to others who need Energy to access more computation temporarily redundancy in a highly efficient, market-driven way.
Advanced Use: Fee Payment in an Escrow by Cryptography
Having an understanding of these fundamentals helps us to appreciate complex services e.g. the possibility to pay a USDT transfer fee with USDT. They are a brilliant (and trust-less) application of cryptography that serve as an automated escrow of sorts, and platforms like Netts make this process even more frictionless.
At the centre of this challenge is an age-old chicken and egg problem: services have to give you Energy before you can send your transfer, but they need some assurance that you will return the favour. The answer is to hold a signed transaction in escrow. And this is not just a promise, this is a contract bound by a cryptography. Only the service is able to successfully broadcast your signed transaction that pays its fee when it receives the transaction. Thus their loan of Energy and TRX is a fully-collateralized, risk-mitigated move. This is complex for the service provider because it all happens under the hood — exposing these multiple WalletConnect adapters, wallet-specific idiosyncrasies, and trying to gracefully orchestrate a multi-stage dance of the transactions so nothing gets broadcast too early.
Resource Calculation Can Be the Most Complex Form of Art
It asks the question, "How much Energy do I need? May look like simple math, but is really complex state check of blockchain. The variables include:
- Amount of USDT: does the address has zero balance of USDT? Otherwise, the TRON network has to assign new storage for it in the USDT contract, which costs nearly twice the Energy (65,000 vs. 131,000).
- Resources of the sender: how many free Bandwidth per day, staked Bandwidth and staked Energy does the sender's address has?
- Account activation: is this address actually live on the network? You'll also incur a small resource fee for activating an address that has never had an outbound transaction.
Manually calculating this is impractical.
Automated tools like the netts.io resource converter are essential. They serve as oracles, querying the TRON blockchain for the state of both the sender and receiver addresses in real-time. They pass the variables through the cost matrix, and this helps to give an accurate calculation allowing users to almost always make the most profitable decision (burn TRX, or rent precisely the right amount of Energy at less than 1/10 the price).
If we take a look under the hood, we find that the simplicity for which the TRON network is known, is actually the result of elegant and solid technical design. This complex system makes for a super quick, secure and extraordinarily efficient ecosystem designed for a worldwide network of its users.